Hi friends this is my first blog post ever and i have shared about SCADA systems which is based upon our(me and my friend Pawan) presentation on the same topic in our college. please send your valuable comments and your ideas about the topic so that i also can get more knowledge about this topic .
SCADA stands for Supervisory Control and Data acquisition which is a process control system that enables a site operator to monitor and control process that is distributed among various remote sites. As such, it is a purely software package that is Positioned on top of hardware to which it is interfaced, in general via Programmable Logic Controllers (PLCs), or other commercial hardware modules. SCADA systems are combination of computers, controllers, instruments; actuators, networks and interfaces that manage the control of automated and allow analysis of those system by data collection and processing.
They are used in most industrial processes: e.g. steel making, power generation (conventional and nuclear) and distribution, chemistry, but also in some experimental facilities such as nuclear fusion. The size of such plants ranges from a few 1000 to several 10 thousands input/output (I/O) channels. However, SCADA systems evolve rapidly and are now penetrating the market of plants with a number of I/O channels of several 100 K: we know of two cases of near to 1 M I/O channels currently under development. SCADA systems used to run on DOS, VMS and UNIX; in recent years all SCADA vendors have moved to NT. One product was found that also runs under Linux.
They are used in most industrial processes: e.g. steel making, power generation (conventional and nuclear) and distribution, chemistry, but also in some experimental facilities such as nuclear fusion. The size of such plants ranges from a few 1000 to several 10 thousands input/output (I/O) channels. However, SCADA systems evolve rapidly and are now penetrating the market of plants with a number of I/O channels of several 100 K: we know of two cases of near to 1 M I/O channels currently under development. SCADA systems used to run on DOS, VMS and UNIX; in recent years all SCADA vendors have moved to NT. One product was found that also runs under Linux.
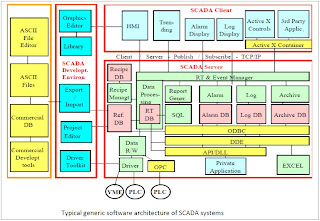
ARCHITECTURE
A SCADA System usually consists of the following subsystems:
* A Human-Machine Interface or HMI is the apparatus which presents process data to a human operator, and through this, the human operator monitors and controls the process.
* A supervisory (computer) system, gathering (acquiring) data on the process and sending commands (control) to the process.
* Remote Terminal Units (RTUs) connecting to sensors in the process, converting sensor signals to digital data and sending digital data to the supervisory system.
* Programmable Logic Controller (PLCs) used as field devices because they are more economical, versatile, flexible, and configurable than special-purpose RTUs.
* Communication infrastructure connecting the supervisory system to the Remote Terminal Units.
First generation: "Monolithic"
In the first generation, computing was done by mainframe computers. Networks did not exist at the time SCADA was developed. Thus SCADA systems were independent systems with no connectivity to other systems. Wide Area Networks were later designed by RTU vendors to communicate with the RTU. The communication protocols used were often proprietary at that time. The first-generation SCADA system was redundant since a back-up mainframe system was connected at the bus level and was used in the event of failure of the primary mainframe system.
Second generation: "Distributed"
The processing was distributed across multiple stations which were connected through a LAN and they shared information in real time. Each station was responsible for a particular task thus making the size and cost of each station less than the one used in First Generation. The network protocols used were still mostly proprietary, which led to significant security problems for any SCADA system that received attention from a hacker. Since the protocols were proprietary, very few people beyond the developers and hackers knew enough to determine how secure a SCADA installation was. Since both parties had invested interests in keeping security issues quiet, the security of a SCADA installation was often badly overestimated, if it was considered at all.
Third generation: "Networked"
These are the current generation SCADA systems which use open system architecture rather than a vendor-controlled proprietary environment. The SCADA system utilizes open standards and protocols, thus distributing functionality across a WAN rather than a LAN. It is easier to connect third party peripheral devices like printers, disk drives, and tape drives due to the use of open architecture. WAN protocols such as Internet Protocol (IP) are used for communication between the master station and communications equipment. Due to the usage of standard protocols and the fact that many networked SCADA systems are accessible from the Internet; the systems are potentially vulnerable to remote cyber-attacks. On the other hand, the usage of standard protocols and security techniques means that standard security improvements are applicable to the SCADA systems, assuming they receive timely maintenance and updates.
I am discussing here more advanced form of SCADA system which was used at CERN.
A. Hardware Architecture
Basic layers in a SCADA system can be classified in two parts generally: the "client layer" which caters for the man machine interaction and the "data server layer" which handles most of the process data control activities. The data servers communicate with devices in the field through process controllers.
Process controllers, e.g. PLCs, are connected to the data servers either directly or via networks or fieldbuses. Data servers are connected to each other and to client stations via an Ethernet LAN. The data servers and client stations are NT platforms but for many products the client stations may also be W95 machines.
Remote Terminal Unit (RTU); The RTU connects to physical equipment. Typically, an RTU converts the electrical signals from the equipment to digital values such as the open/closed status from a switch or a valve, or measurements such as pressure, flow, voltage or current. By converting and sending these electrical signals out to equipment the RTU can control equipment, such as opening or closing a switch or a valve, or setting the speed of a pump.
Supervisory Station; The term "Supervisory Station" refers to the servers and software responsible for communicating with the field equipment (RTUs, PLCs, etc), and then to the HMI software running on workstations in the control room, or elsewhere. In smaller SCADA systems, the master station may be composed of a single PC. In larger SCADA systems, the master station may include multiple servers, distributed software applications, and disaster recovery sites. To increase the integrity of the system the multiple servers will often be configured in a dual-redundant or hot-standby formation providing continuous control and monitoring in the event of a server failure.
B. Software Architecture
The products are multi-tasking and are based upon a real- time database (RTDB) located in one or more servers. Servers are responsible for data acquisition and handling.
(E.g. polling controllers, alarm checking, calculations, logging and archiving) on a set of parameters, typically those they are connected to. However, it is possible to have dedicated servers for particular tasks, e.g. data logger a SCADA architecture that is generic for the products that were evaluated.
C. Human-Machine interface (HUI).
A Human-Machine Interface or HMI is the apparatus which presents process data to a human operator, and through which the human operator controls the process. An HMI is usually linked to the SCADA system's databases and software programs, to provide trending, diagnostic data, and management information such as scheduled maintenance procedures, logistic information, detailed schematics for a particular sensor or machine, and expert-system troubleshooting guides. The HMI system usually presents the information to the operating personnel graphically, in the form of a mimic diagram. This means that the operator can see a schematic representation of the plant being controlled.
D. Communications
*Internal Communication*
Server-client and server-server communication is in general on a publish-subscribe and event-driven basis and uses a TCP/IP protocol, i.e., a client application subscribes to a parameter which is „owned‟ by a particular server application and only changes to that parameter are then communicated to the client application.
*Access to Devices*
The data servers poll the controllers at a user define polling rate. The polling rate may be different for different parameters. The controllers pass the requested parameters to the data servers. Time stamping of the process parameters is typically performed in the controllers and this time-stamp is taken over by the data server. If the controller and communication protocol used support unsolicited data transfer then the products will support this too. The products provide communication drivers for most of the common PLCs and widely used field-buses, e.g., Modbus. Of the three fieldbuses that are recommended at CERN, both Profibus and Worldfip are supported but CANbus often not [3]. Some of the drivers are based on third party products (e.g., Applicom cards) and therefore have additional cost associated with them. VME on the other hand is generally not supported.
A single data server can support multiple communications protocols: it can generally support as many such protocols as it has slots for interface cards. The effort required to develop new drivers is typically in the range of 2-6 weeks depending on the complexity and similarity with existing drivers, and a driver development toolkit is provided.
E. Interfacing
Application Interfaces / Openness The provision of OPC client functionality for SCADA to access devices in an open and standard manner is developing. There still seems to be a lack of devices/controllers, which provide OPC server software, but this improves rapidly as most of the producers of controllers are actively involved in the development of this standard. OPC is currently being evaluated by the CERN-IT-CO group [4].
The products also provide
* an Open Data Base Connectivity (ODBC) interface to the data in the archive/logs, but not to the configuration database,
* an ASCII import/export facility for configuration data,
* a library of APIs supporting C, C++, and Visual Basic (VB) to access data in the RTDB, logs and archive. The API often does not provide access to the product‟s internal features such as alarm handling, reporting, trending, etc.
The PC products provide support for the Microsoft standards such as Dynamic Data Exchange (DDE) which allows e.g. to visualize data dynamically in an EXCEL spreadsheet, Dynamic Link Library (DLL) and Object Linking and Embedding (OLE).
*Database*
The configuration data are stored in a database that is logically centralized but physically distributed and that is generally of a proprietary format. For performance reasons, the RTDB resides in the memory of the servers and is also of proprietary format. The archive and logging format is usually also proprietary for performance reasons, but some products do support logging to a Relational Data Base Management System (RDBMS) at a slower rate either directly or via an ODBC interface.
F. Scalability
Scalability is understood as the possibility to extend the SCADA based control system by adding more process variables, more specialized servers (e.g. for alarm handling) or more clients. The products achieve scalability by having multiple data servers connected to multiple controllers. Each data server has its own configuration database and RTDB and is responsible for the handling of a sub-set of the process variables (acquisition, alarm handling, archiving.
G. Redundancy
The products often have built in software redundancy at a server level, which is normally transparent to the user. Many of the products also provide more complete redundancy solutions if required.
FUNCTIONALITY
A. Access Control
Users are allocated to groups, which have defined read/write access privileges to the process parameters in the system and often also to specific product functionality.
B. MMI
The products support multiple screens, which can contain combinations of synoptic diagrams and text. They also support the concept of a "generic" graphical object with links to process variables. These objects can be “dragged and dropped” from a library and included into a synoptic diagram. Most of the SCADA products that were evaluated decompose the process in “atomic” parameters (e.g. a power supply current, its maximum value, it‟s on/off status, etc.) to which a Tag-name is associated. The Tag-names used to link graphical objects‟ to devices can be edited as required. The products include a library of standard graphical symbols, many of which would however not be applicable to the type of applications encountered in the experimental physics community.
Standard windows editing facilities are provided: zooming, re-sizing, scrolling... On-line configuration and customization of the MMI is possible for users with the appropriate privileges. Links can be created between display pages to navigate from one view to another.
C. Trending
The products all provide trending facilities and one can summaries the common capabilities as follows:
* The parameters to be trended in a specific chart can be predefined or defined on-line.
* A chart may contain more than 8 trended parameters or pens and an unlimited number of charts can be displayed (restricted only by the readability).
* Real-time and historical trending are possible, although generally not in the same chart.
* Historical trending is possible for any archived parameter.
* Zooming and scrolling functions are provided.
* Parameter values at the cursor position can be displayed.
The trending feature is either provided as a separate module or as a graphical object (ActiveX), which can then be embedded into a synoptic display. XY and other statistical analysis plots are generally not provided.
D. Alarm Handling
Alarm handling is based on limit and status checking and performed in the data servers. More complicated expressions (using arithmetic or logical expressions) can be developed by creating derived parameters on which status or limit checking is then performed. The alarms are logically handled centrally, i.e., the information only exists in one place and all users see the same status (e.g., the acknowledgement), and multiple alarm priority levels (in general many more than 3 such levels) are supported. It is generally possible to group alarms and to handle these as an entity (typically filtering on group or acknowledgement of all alarms in a group). Furthermore, it is possible to suppress alarms either individually or as a complete group. The filtering of alarms seen on the alarm page or when viewing the alarm log is also possible at least on priority, time and group. However, relationships between alarms cannot generally be defined in a straightforward manner. E- mails can be generated or predefined actions automatically executed in response to alarm conditions.
E. Logging/Archiving
The terms logging and archiving are often used to describe the same facility. However, logging can be thought of as medium-term storage of data on disk, whereas archiving is long-term storage of data either on disk or on another permanent storage medium. Logging is typically performed on a cyclic basis, i.e., once a certain file size, time period or number of points is reached the data is overwritten. Logging of data can be performed at a set frequency, or only initiated if the value changes or when a specific predefined event occurs. Logged data can be transferred to an archive once the log is full. The logged data is time-stamped and can be filtered when viewed by a user. The logging of user actions is in general performed together with either a user ID or station ID. There is often also a VCR facility to play back archived data.
F. Report Generation
One can produce reports using SQL type queries to the archive, RTDB or logs. Although it is sometimes possible to embed EXCEL charts in the report, a “cut and paste” capability is in general not provided. Facilities exist to be able to automatically generate print and archive reports.
G. Automation
The majority of the products allow actions to be automatically triggered by events. A scripting language provided by the SCADA products allows these actions to be defined. In general, one can load a particular display, send an Email, run a user defined application or script and write to the RTDB.
The concept of recipes is supported, whereby a particular system configuration can be saved to a file and then re-loaded at a later date.
Sequencing is also supported whereby, as the name indicates, it is possible to execute a more complex sequence of actions on one or more devices. Sequences may also react to external events.
Some of the products do support an expert system but none has the concept of a Finite State Machine (FSM).
APPLICATION DEVELOPMENT
A. Configuration
The development of the applications is typically done in two stages. First the process parameters and associated information (e.g. relating to alarm conditions) are defined through some sort of parameter definition template and then the graphics, including trending and alarm displays are developed, and linked where appropriate to the process parameters. The products also provide an ASCII Export/Import facility for the configuration data (parameter definitions), which enables large numbers of parameters to be configured in a more efficient manner using an external editor such as Excel and then importing the data into the configuration database.
However, many of the PC tools now have a Windows Explorer type development studio. The developer then works with a number of folders, which each contains a different aspect of the configuration, including the graphics.
The facilities provided by the products for configuring very large numbers of parameters are not very strong. However, this has not really been an issue so far for most of the products to-date, as large applications are typically about 50K I/O points and database population from within an ASCII editor such as Excel is still a workable option.
On-line modifications to the configuration database and the graphics are generally possible with the appropriate level of privileges.
B. Development Tools
The following development tools are provided as standard:
* a graphics editor, with standard drawing facilities including freehand, lines, squares circles, etc. It is possible to import pictures in many formats as well as using predefined symbols including e.g. trending charts, etc. A library of generic symbols is provided that can be linked dynamically to variables and animated as they change. It is also possible to create links between views so as to ease navigation at run-time.
* a data base configuration tool (usually through parameter templates). It is in general possible to export data in ASCII files so as to be edited through an ASCII editor or Excel.
* a scripting language
* an Application Program Interface (API) supporting C, C++, VB
* a Driver Development Toolkit to develop drivers for hardware that is not supported by the SCADA product.
C. Object Handling
The products in general have the concept of graphical object classes, which support inheritance. In addition, some of the products have the concept of an object within the configuration database. In general the products do not handle objects, but rather handle individual parameters, e.g., alarms are defined for parameters, logging is performed on parameters, and control actions are performed on parameters. The support of objects is therefore fairly superficial
SECURITY ISSUES
The move from proprietary technologies to more standardized and open solutions together with the increased number of connections between SCADA systems and office networks and the Internet has made them more vulnerable to attacks. Consequently, the security of SCADA-based systems has come into question as they are increasingly seen as extremely vulnerable to cyber warfare/cyber terrorism attacks.
In particular, security researchers are concerned about:
* the lack of concern about security and authentication in the design, deployment and operation of existing SCADA networks
* the belief that SCADA systems have the benefit of security through obscurity through the use of specialized protocols and proprietary interfaces
* the belief that SCADA networks are secure because they are physically secured
* the belief that SCADA networks are secure because they are disconnected from the Internet.
EVOLUTION
SCADA vendors release one major version and one to two additional minor versions once per year. These products evolve thus very rapidly so as to take advantage of new market opportunities, to meet new requirements of their customers and to take advantage of new technologies. most of the SCADA products that were evaluated decompose the process in “atomic” parameters to which a Tag-name is associated. This is impractical in the case of very large processes when very large sets of Tags need to be configured. As the industrial applications are increasing in size, new SCADA versions are now being designed to handle devices and even entire systems as full entities (classes) that encapsulate all their specific attributes and functionality. In addition, they will also support multi-team development. As far as new technologies are concerned, the
SCADA products are now adopting:
* Web technology, ActiveX, Java, etc.
* OPC as a means for communicating internally between the client and server modules. It should thus be possible to connect OPC compliant third party modules to that SCADA product.
ENGINEERING
One should rightly anticipate significant development and maintenance savings by adopting a SCADA product for the implementation of a control System. The need for proper engineering can‟t be sufficiently emphasized to reduce development effort and to reach a system that complies with the requirements, that is economical in development and maintenance and that is reliable and cheap. Examples of engineering activities specific to the use of a SCADA system are the definition of:
* a library of objects (PLC, device, subsystem) complete with standard object behavior (script, sequences, ...), graphical interface and associated scripts for animation,
* templates for different types of "panels", e.g.
alarms,
* instructions on how to control e.g. a device ...,
* a mechanism to prevent conflicting controls (if not provided with the SCADA),
* alarm levels, behavior to be adopted in case of specific alarms, ...
TRENDS IN SCADA
North American Electric Reliability Corporation has specified that electrical system data should be time-tagged to the nearest millisecond. Electrical system SCADA systems provide this Sequence of events recorder function, using Radio clocks to synchronize the RTU or distributed RTU clocks.
SCADA systems are coming in line with standard networking technologies. Ethernet and TCP/IP based protocols are replacing the older proprietary standards. Although certain characteristics of frame-based network communication technology (determinism, synchronization, protocol selection, environment suitability) have restricted the adoption of Ethernet in a few specialized applications, the vast majority of markets have accepted Ethernet networks for HMI/SCADA.
A few vendors have begun offering application specific SCADA systems hosted on remote platforms over the Internet.
SCADA systems are becoming increasingly ubiquitous. Thin clients, web portals, and web based products are gaining popularity with most major vendors. The increased convenience of end users viewing their processes remotely introduces security considerations. While these considerations are already considered solved in other sectors of Internet services, not all entities responsible for deploying SCADA systems have understood the changes in accessibility and threat scope implicit in connecting a system to the Internet.
POTENTIAL BENEFITS OF SCADA
The benefits one can expect from adopting a SCADA system for the control of experimental physics facilities can be summarized as follows:
* A rich functionality and extensive development facilities. The amount of effort invested in SCADA product amounts to 50 to 100 p-years!
* The amount of specific development that needs to be performed by the end-user is limited, especially with suitable engineering.
* Reliability and robustness. These systems are used for mission critical industrial processes where reliability and performance are paramount. In addition, specific development is performed within a well-established framework that enhances reliability and robustness.
* Technical support and maintenance by the vendor.
Using a SCADA system for the controls ensures a common framework not only for the development of the specific applications but also for operating the detectors. Operators experience the same "look and feel" whatever part of the experiment they control. However, this aspect also depends to a significant extent on proper engineering.
The contents in this article is inspired by our abstract on the same paper which we have prepared by the help of some online articles, books and our understanding on the topic. I welcome any comment on the topic.


No comments:
Post a Comment